如果能结合其他漏洞利用,才算危险点,不然只能算风险点
PHP变量覆盖
以下函数或语法可能导致变量覆盖的产生
$$
extract()
parse_str()
import_request_variables()
mb_parse_str
register_globalsextract()
extract()函数从数组将变量导入当前的符号表
<?php
$dada = "safe_value";
extract($_GET);
echo $dada;
?>
/*假设构造了如下URL
http://example.com/vulnerable.php?dada=malicious_value
将会把$dada覆盖成malicious_value$$
$$语法被称为可变变量
test = hello => 
//base.php
<?php
foreach ($_GET as $key => $value) {
$$key = $value;
}
?>
//admin.php
<?php
require 'base.php';
//$is_login = false;
foreach ($_GET as $key => $value) {
$$key = $value;
}
$data = query_from_db();
$usermane = $data('usermane');
$password = $data('password');
if ($username == "admin" && $password == "asdaxxsdasdasd") {
$is_login = true;
}
if ($is_login){
eval($dada);
}
?>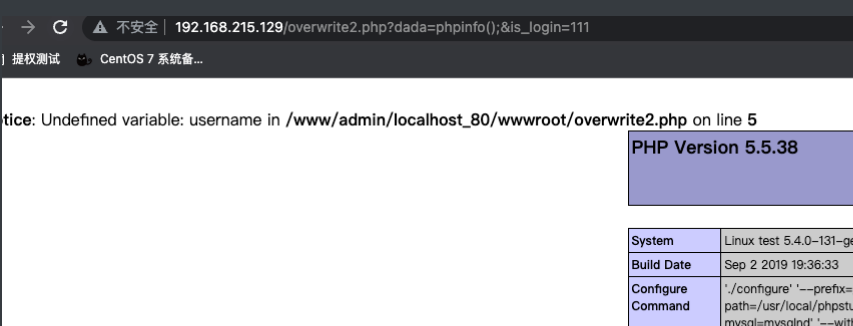
这里给变量$is_login赋值的机会让$is_login直接为true






Comments NOTHING